July 11, 2023
A common misconception about cyber security, is that you simply need to buy a product or two to ‘protect your data’. It would be nice if the things worked that way, but IT environments are simply too complex and the range of threats you face are far too varied and dynamic. So, what can you do when any part of your network, infrastructure, devices or applications can be exploited from vulnerabilities you didn’t even know existed? How can you defend against that? Well, you can’t plug a hole you can’t see. It therefore becomes crucial to first identify and then manage or remediate those vulnerabilities.
Concepts like ‘vulnerabilities’, ‘vulnerability management’, and ‘remediation’ can seem like a convoluted word salad of tech-speak. However, they are genuinely important, so let’s try to untangle these complex ideas and shed light on their crucial roles in fortifying your business’s digital operations.
Let’s delve deeper into the evolving world vulnerability management and the often underemphasised yet critical role of remediation in enhancing your security posture.
DECIPHERING THE TECH LINGO: VULNERABILITIES AND THEIR MANAGEMENT
Let’s begin with an analogy. Picture your business’s digital infrastructure as a castle, safeguarding your most valuable asset—your data. Imagine, though, that there could be hidden trapdoors or weaker sections in the castle walls that could let potential attackers sneak in. These are what we refer to as ‘vulnerabilities’.
Now, vulnerability management comes into the picture as the process of identifying, assessing, treating, and reporting on these security weaknesses. It’s a continuous cycle that requires proactive scanning and evaluation of potential threats. But there’s one key aspect that often goes underappreciated: Remediation.
ACTING PROMPTLY: THE CRITICAL ROLE OF REMEDIATION
Spotting a weak wall or a hidden trapdoor in your castle is pointless if it isn’t addressed promptly. This is where remediation—the action taken to fix these identified vulnerabilities—comes into play. Remediation could involve applying patches, reconfiguring security settings, or even overhauling certain systems to improve security.
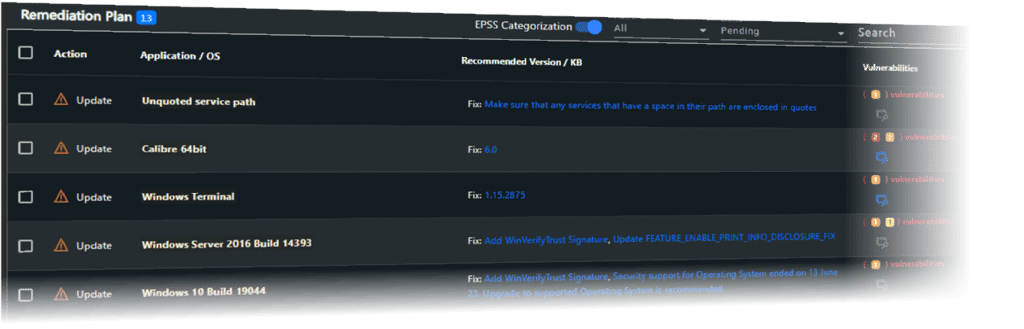
WHY IS REMEDIATION ESSENTIAL IN YOUR SECURITY STRATEGY?
While many MSPs are adept at providing vulnerability reports, they often stop there, leaving the essential step of remediation unattended unless specifically paid to do so. This approach leaves a critical gap in your security strategy, where known weaknesses are left unresolved, posing substantial risks.
However, our approach includes remediation as an essential component of our vulnerability management service. We understand that identifying vulnerabilities without acting upon them is akin to acknowledging a leaky tap but allowing it to continue dripping.
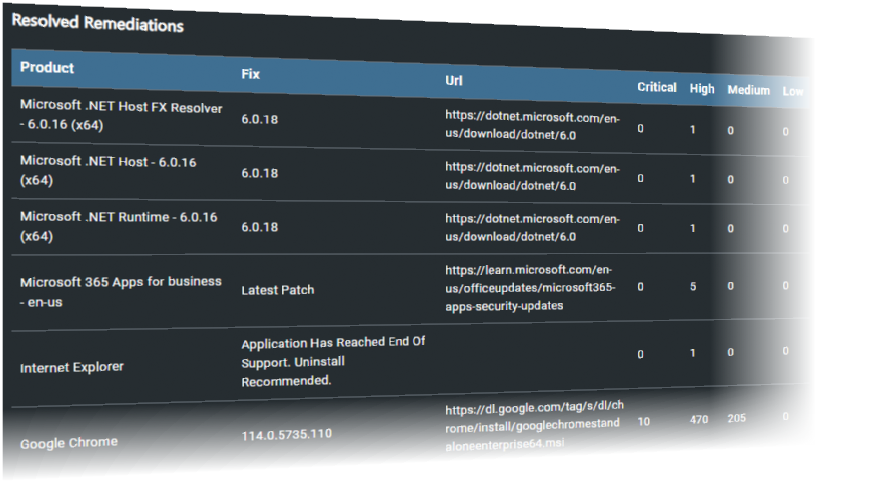
Remediation completes the loop in vulnerability management. It addresses identified vulnerabilities, reducing the available attack surface and enhancing your security posture. This is especially critical in today’s dynamic digital world, where new vulnerabilities emerge daily, and cybercriminals are constantly upping their game.
By ensuring remediation as part of our services, we not only help identify potential threats but also take decisive action to neutralise them. This comprehensive approach ensures that your digital castle remains impregnable against potential breaches.
GOING THE EXTRA MILE: COMPLIANCE AND PEACE OF MIND
Comprehensive vulnerability management, including remediation, not only bolsters your digital operations’ security but also assists in meeting compliance requirements. Whether it’s GDPR, HIPAA, PCI-DSS, or any other industry standard, a demonstrated commitment to vulnerability management—and crucially, remediation—provides evidence of your robust cybersecurity approach.
THE BOTTOM LINE
In summary, remediation is not just an added perk—it’s a necessity. It transforms vulnerability management from a mere reporting process into a dynamic, responsive security strategy. As your dedicated MSP, we’ll ensure that every hidden trapdoor or weak wall is not only identified but promptly addressed, providing a comprehensive shield against cyber threats. That way, you can focus on what you do best—running and growing your business.

